
iClicker fake captcha security incident
Summary
The iClicker service provider, Macmillan Learning, notified the University of Colorado Boulder that the primary iClicker website (www.iclicker.com) was compromised by an attacker between April 12-16, 2025. The compromise, which utilized a malicious captcha, did not impact the iClicker app or any data stored on iClicker systems. The CU information security team has assessed the incident information provided by Macmillan and has determined there was minimal exposure and a low risk level for our campus users.
CU Boulder impact
During the compromise window, just under 14,000 CU Boulder iClicker users visited the iClicker site. Please note, this compromise did not impact the iClicker app or any data stored on iClicker systems.
Compromise details
During the compromise window, the attacker was able to implement a malicious captcha on the iclicker.com login page. Similar attacks generally download and install malicious software used for various purposes including ransomware, botnet construction, and personal information gathering. Based on the information provided by Macmillan, we are aware of only one CU Boulder user who followed the prompts of the malicious captcha.
Below is an example of a fake captcha.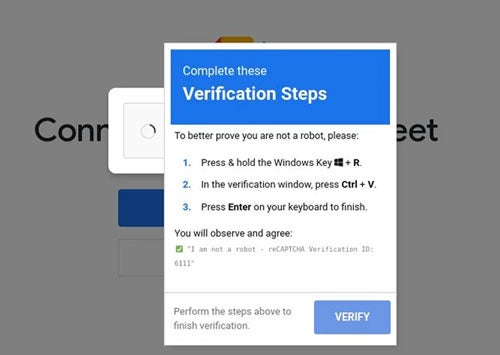
If you interacted with the fake captcha
If you are concerned that you may have followed the prompts of the captcha during the attack window (April 12-16), the CU information security team recommends that you run a full security scan of the devices you used to visit the iClicker site (www.iclicker.com). If you would like help to run a security scan, please contact the IT Service Center at oithelp@colorado.edu or 303-735-4357.
How to protect yourself
Endpoint detection and response software provides protection from security threats like malware and ransomware. The university recommends multiple endpoint detection and response solutions. While the university uses technology to block malicious software downloads, phishing emails and websites, this technology complements the responsibility we all have to be conscientious internet users.
Even though this website compromise was on a trusted website, it’s important to note that legitimate captcha functionality will never ask you to take actions on your device outside of the dialog box it is contained in. The fact that this attack requested users to open a Windows run dialog box and run code that was on the clipboard is extremely suspicious.
If you ever have questions about the legitimacy of a website or any other IT technology, you are welcome to contact CU Boulder’s IT Service Center at oithelp@colorado.edu or 303-735-4357. Learn more about CU Boulder’s IT Service Center and their hours of operation.