Uploading A Device to Autopilot
New machines purchased through the Dell punch-out on CU Marketplace will be automatically enrolled in our tenant and Autopilot (AP) once the program launches. Ensure that your orders include your department code as the Group Tag when prompted.
For all other machines, including devices you would like to test, follow OIT's preferred method, the Out of Box Experience instructions below, using the CU Autopilot Enrollment exe file.
If that is unsuccessful, you can use OIT's back up enrollment method and run a PowerShell script, then upload the resulting CSV to Intune. Machines added in this way have a delay of about an hour before they can run through AP once the CSV is uploaded.
Preferred Method: Out of Box Experience (OOBE)
Follow these instructions if you need to enroll a computer that is on the initial Windows setup screen, or follow the steps in our Enroll a Windows computer tutorial:
- On another computer, copy the CU Autopilot Enrollment.exe file to a USB flash drive.
- On the new computer, if it is in the Out of Box Experience (initial Windows setup), press Shift-F10 to open a command prompt and continue to step 3. If the computer is already signed in to Windows with a user profile, open Windows File Explorer and skip to step 5.
- Type explorer.
- Press enter.
- You will now have a Windows File Explorer window open. Navigate to your USB flash drive and run the CU Autopilot Enrollment.exe.
- Select a Department Abbreviation if applicable.
- Click Enroll Online. If you are on campus or connected to the VPN, your registration will complete. If not and the enrollment fails, click Create CSV (manual). You can save the file to the flash drive, or if you've connected to a network, you can upload the file to a file server.
- If you had to use the Create CSV (manual) process on step 6, you will need to navigate to the Secure Computing Opt-In - Windows form and submit the .CSV file you have created on another computer.
- Wait 30 minutes after your enrollment is complete before proceeding.
- If your new computer is in the Out of Box Experience, reboot. If your computer is signed into a user profile, follow Microsoft's instructions to reset the computer.
- The new computer is now ready to be deployed to the end user, who can begin the Autopilot process when prompted for their email address.
Other Enrollment Method: HWID Instructions for Purchases Made Outside the Dell Punchout in Marketplace
You need to be able to run an admin PowerShell prompt (this can also be done in the OOBE before a customer ever tries to configure the device or in a PE using shift + f10, but I would not recommend having a user try and do this piece)
- The commands you need to run are:
New-Item -Type Directory -Path "C:\HWID"Set-Location -Path "C:\HWID"Set-ExecutionPolicy -Scope Process -ExecutionPolicy UnrestrictedInstall-Script -Name Get-WindowsAutoPilotInfoGet-WindowsAutoPilotInfo.ps1 -OutputFile AutoPilotHWID.csv - At the end, the autopilotHWID.csv will be in the C:\HWID folder. You need to grab this file (net-use for a server, or you can use explorer.exe to open up the GUI if you're doing this from OOBE)
- Add a Group Tag to the CSV, the image below shows what the CSV should look like.
- The easiest way to accomplish this from the pre-generated CSV is to:
- Open the CSV with Excel
On the Data Tab, select: Text to Columns
- Select Delimited, then hit Next
- Now add a final Column in D Titled Group Tag and then add your Department Code as the Group Tag in the corresponding row. Make sure to save the result as a .CSV as it cannot work with the default .xlsx file.
The initial CSV will look something like:
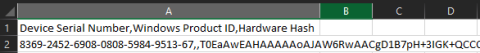
Note: a VM was used in the picture above so the Device Serial Number is much longer than a regular piece of hardware will typically show.
- After adding Group Tag and correct formatting:
- Multiple devices can be added to a single CSV as well and can have either the same or different Group Tags:
Management Areas and Basic Information
On Premises Active Directory (ad.colorado.edu)
Machines going through Autopilot automatically bind with both the Azure Active Directory and ad.colorado.edu.
All devices going through Autopilot bind to a sub-OU of the Campus Certified Computers OU determined by the Group tag. For any group tag that has a configured workflow (this requires working with EMS to set up), it will drop into the departmental OU. Devices that do not have a matching Group tag will drop into the unmanaged UCB OU that receives default Secure Compute policy. Default devices should be fully compliant with the new security policy without further customization.
All OUs exist within: OU=Campus Certified Computers,OU=Departments Schools and Colleges,DC=ad,DC=colorado,DC=edu

Departmental OUs are managed by the department’s admins. Each admin has the ability to move, create, delete, and rename devices and groups as well as manage any desired sub-OUs. You also have the ability to link any group policy to manage those devices
Management of the Active Directory for Computers, Groups, and OUs is done through dsa.msc (Active Directory Users and Computers snap-in). For Group Policy, use gpmc.msc (Group policy Management Snap in). Both are installed through the RSAT package (Remote Serve Administration Tools) downloadable from Microsoft. Administrators must use a SuperUser account for managing infrastructure resources, no regular identikeys can be used.
Departmental Administrators are responsible for managing their own OUs.At a minimum, log in and administrator rights need to be assigned to any managed OU as that is not done by default.In the unmanaged OU, the enrolling Autopilot user is made an Admin, but this behavior is not default in departmental OUs. Onedrive Folder Redirection is also not included by default. Either (or both) of these policies can be applied to a managed OU by linking OIT - DS - Autopilot - Exclusive Admin Logon DDSDeployfor enrolling users receiving Admin and OIT - DS - Autopilot - OneDrive Folder Redirection to enable OneDrive folder redirection. You can also create your own policies if you want or need more control over the policies.
All default security policy to accomplish the Secure Compute requirements are linked at the Campus Certified Computers level and can be viewed by any administrator that wishes to review them. The settings are not enforced, which means that any of the policies that are problematic can be overwritten with a conflicting policy linked at the department OU level as it will have priority.
As with any customization, it is possible to customize systems in a way that no longer meets all of the Secure Compute standards. Be sure to consult security before making any necessary changes which would negatively impact the security of the systems.
Autopilot, Intune, and Azure
Azure (and specifically Azure Active Directory) is Microsoft’s cloud platform. Intune is the endpoint management space of the Azure cloud, and it is used for some device configurations. Intune is also the platform that manages Autopilot workflows.Autopilot is a tool for configuring devices as they go through the OOBE (Out of Box Experience) so that they become compliant with Secure Compute without IT intervention during machine deployment and reimaging.
Any device that does not go through the OOBE will also not go through Autopilot. This means that any imaging process that skips the OOBE (this is most of them) will also skip Autopilot. For Autopilot to run, it also needs an internet connection available when the device is first powered on so that it can check for an available profile.A device that skips Autopilot will not attempt to go through it until the next time the hardware reaches the OOBE, which only occurs after a reimage or reset.
Autopilot can be performed anywhere there is an internet connection, you do not need to be on campus to configure a new device. This is a great tool for remote deployments as well as provides great tools for remote troubleshooting that traditional imaging does not give you.
Autopilot is the process that binds the device to both Azure Active Directory and the AD. It does the AD join through a process known as an offline domain join which means that the computer does not need line of sight to a domain controller to complete the join. This means that Autopilot can be performed from anywhere. The offline domain join also creates a new machine object each time that a device goes through Autopilot. Machines will never reuse their old object if they go through Autopilot again.
Once presented with a log on screen, users log in with their identikey. A machine authenticated always on VPN is installed by Autopilot which allows users to authenticate for the first time regardless of where they enrolled the device.
Autopilot upgrades the default Windows Pro installation from dell to Windows Enterprise. Machines need to be ordered with Windows for Autopilot to work, and it is also required to compliant with campus licensing.
Autopilot installs Office, the Cisco VPN, Chrome, and Firefox while all other installs are performed through MCM. These components are configurable (though removing the VPN will result in systems being unable to perform first log ins from off campus). Configuration of Intune and Autopilot can be delegated should you need or want the control. EMS’ recommendation is not to perform configurations to those spaces, at least initially, as there is not much to configure within the Azure space that is not better accomplished through other tools.
MCM (Microsoft Configuration Manager)
MCM is the primary technology used to manage applications, application updates, and OS updates. It also performs several reporting functions.By default, MCM will keep the OS patched as well as a wide variety of common software. Reboots, when necessary for updates to complete, are also enforced by MCM. Patches are deployed to end users on Fridays, but the reboot is on hold until later. This reboot process is kicked off during the maintenance window, which occurs on Wednesdays. There is a 24-hour countdown ending in a forced reboot if the user has not already done so.
MCM customizations are available, but access to them is a paid service. With MCM access, you can manage patch deployments and timing, application deployments, and a very wide variety of other management options. MCM is a very large, complicated product that also has a mandatory training requirement for admins who would administrate with it.
Maintenance Window exemptions will be available through the regular exemption process (not yet completed) and do not require paid access into MECM to accomplish for individual machines.
Other Notable technologies
Always On VPN (AOVPN)
The AOVPN is a Cisco VPN that uses machine certificates for authentication rather than user credentials. It is enabled as a machine starts up, which allows communication with the Domain Controllers prior to user logins for policy and account credential verification. This VPN will automatically disconnect if a user engages another Cisco VPN connection (such as any private departmental campus VPN). The management tunnel does not automatically disconnect for non-Cisco VPNs such as Juniper. For those, an exception for the Always on VPN may be necessary.
Defender for Endpoint
Defender for Endpoint is configured as a standard part of the Autopilot deployment workflow. It’s done by an MCM deployment that delivers an enrollment package that tells the device to relay security information to CU’s Azure tenant. Customers using AD or MCM customizations may also have their Endpoints tagged in Security Center (not to be confused with Group Tags) so that they can be viewed in the Security Center Azure Portal.
Single Sign-On
Secure Computing devices will automatically use Single Sign-On to log in to OneDrive and Office. This is separate from enabling user folder redirection to OneDrive, which is an available policy for managed devices but not a default.
Company Portal
This is the unified Self-Service portal that combines all available deployments from both Intune and MCM into a single view. Any software that is either generally available or deployed as available to a department customizing their software deployments will appear here for users to install.
